Certified Secure .NET Developer (CSDD™)
About The Course
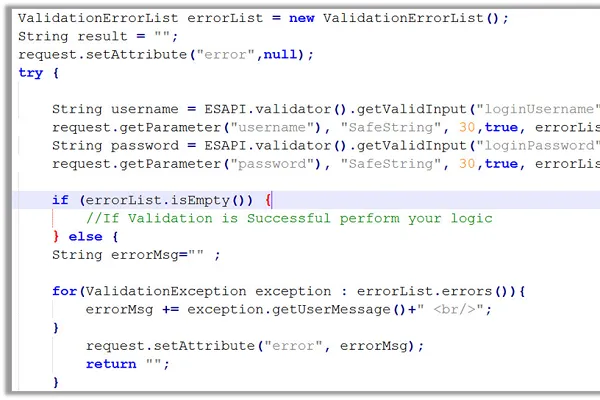
The course will present security guidelines and considerations in .NET applications development. The participants will learn the basics of application security, how to enforce security on a .NET application, using .NET crypto API and other security related issues. In addition, the course presents an overview of .NET's Security Framework, including authentication and authorization implementation.
Objectives of the course
Upon completion of this course, participants will be able to:
- Understand the need for security
- Understand the security threats
- Implement code security best practices
- Implement role based security
- Improve security of ASP.NET Applications
Who should attend this course?
- .NET developers wishing to improve their security skills
Table of Contents










Shakti Ahmed Mavati
Excellent course and trainer explained very well
Aniket Anant Harer
Good training for software developer who aware about security
Jyoti Bhandari
It was a relevant training and benefit for safe web app development
Darshan D Joshi
Good course content & good for novoice developers.
Mrudual Ghagor
Training was interesting
Raushan Kumar
good
Ibrahim Mirza
Good course for the bignners in Corporates for sdecure coding
Akshay N Ajankar
Course was good and its helpful for our company
Amit Rana
Course helps developers to develope applications that are less hackable
Josana Sahare
Good
Akshay Sharad Shingate
It is very much useful to resolve VAPT points in out applications.
Vivek Suryabhan Kasar
It was all good, cleverly helped understand each concept with adherence to the example which were self explanatory.
Nakul V Khatu
Good course
Rohit V Patil
Good course for developer to improve security.
Shweta Vasant Sherlekar
Was good experiance
Roshan Vijay Mehta
It is very useful for secure Applicaton development
Tushar Yuvaraj Gite
Hacking
Nirav Parikh
Training was apt with latest content. Trainer was very knowledgeable and had help to solve our queries.
Tushar Thorat
Good.
Nairit Adhikary
Trainer was very interactive and have provided very simple examples to understand better.
Sunita More
Training was helpful for the development purpose . Got clearance how we can fix the issues related to security.
Ravindra Hirlekar
Course content coverage was good and trainer is also knowledgeable.
Saikrishna Sanka
Overall training was good,the instructor/ training faculty was good in solving the doubts raised with examples.
Moin Ansari
Overall good learning experience.
Sandra Rebells
Sessions were good & will help us to maintain security at code using different techniques including the one explained in training.
Nusrat Khan
Thanks Bhamini Shah for the training, it will benefit to us in future.
Swetha Narayan (Senior Software Engineer)
Prompt in his teachings with adequate knowledge in the areas of Secure Coding.
Abhineet Gosain (Sr. software Engineer)
Good work.
Ganesh Palani
Session was good. Vaibhav was able to show the scenarios in detail with various examples.
Satosh Kumar Mishra (QA)
Presentation is helpful in understanding
V. Venkatesh (Lead SSF)
Session was good. Vaibhav was able to explain the topics in depth and in simple terms.
JeyaKumar N. (Lead DB Engineer)
Training is extremely helpful in identifying injection issues across Web application and underlying databases.
Binu K (Senior Engineering Manager)
Vaibhav has lots of knowledge in OWASP-10 vulnerabilities, was going in depth for few vulnerabilities like SQL injection, XSS, CSRF, etc.
Dilip Janakeeram (QA Engineer)
Training topics covered was interesting and was able to corelate with own daily work.
Avalur Muthya (QA Engineer)
The trainer was very good, but the class would be more interactive.
Pooja Shetty (Senior QA Engineer)
Training was very much informative. Trainer had good knowledge on the area, he was able to answer/explain to use effectively.
Eknath Parkhe, Software Developer, GCO
Training is good. Mahesh take us deep into vulnerabilities like SQL injection. Cross site scripting, Direct data object etc.
Makarand Gharat, Operation Manager, GCO
Training is really good and Mahesh is very knowledgeable. We got very useful information and we will implement this knowledge in our application.
Prasad Thakur, Team Manager, GCO
Excellent knowledge and ability to store the same. Interacting session with all queries answered with detailing.
Sachidanand B Gaikwad, DBA, GCO
Training is very informative. Mahesh explained things very well. Material information provided by him is very useful. Will help to take security measurement in our application.
Girish Dhudhane, Post, AGS House
She is very dedicated towards work,knowledge and detail oriented. I would like to take this chance to Thank You for being such a remarkable trainer
Suyash Korde, AGS House
Shared good practices to be followed during ADLC and Practical examples were also explained
Keith D’souza, AGS House
It was a good training session although if proper scheduling with topic types would have been better
Chand Babu Shaikh, AGS House
Informative knowledge material and trainer was good
Diksha Walunj, AGS House
She was interactive. Able to give more information related to topics. She was trying to solve our queries
Indrani Maiti, AGS House
Informative Knowledge material and trainer was good
Sandeep Pawar, AGS House
Much needed training
Yadnya Nar, AGS House
Training was good relatable topics. Overall very good training by very good trainer