Source Code Analysis
About This Course
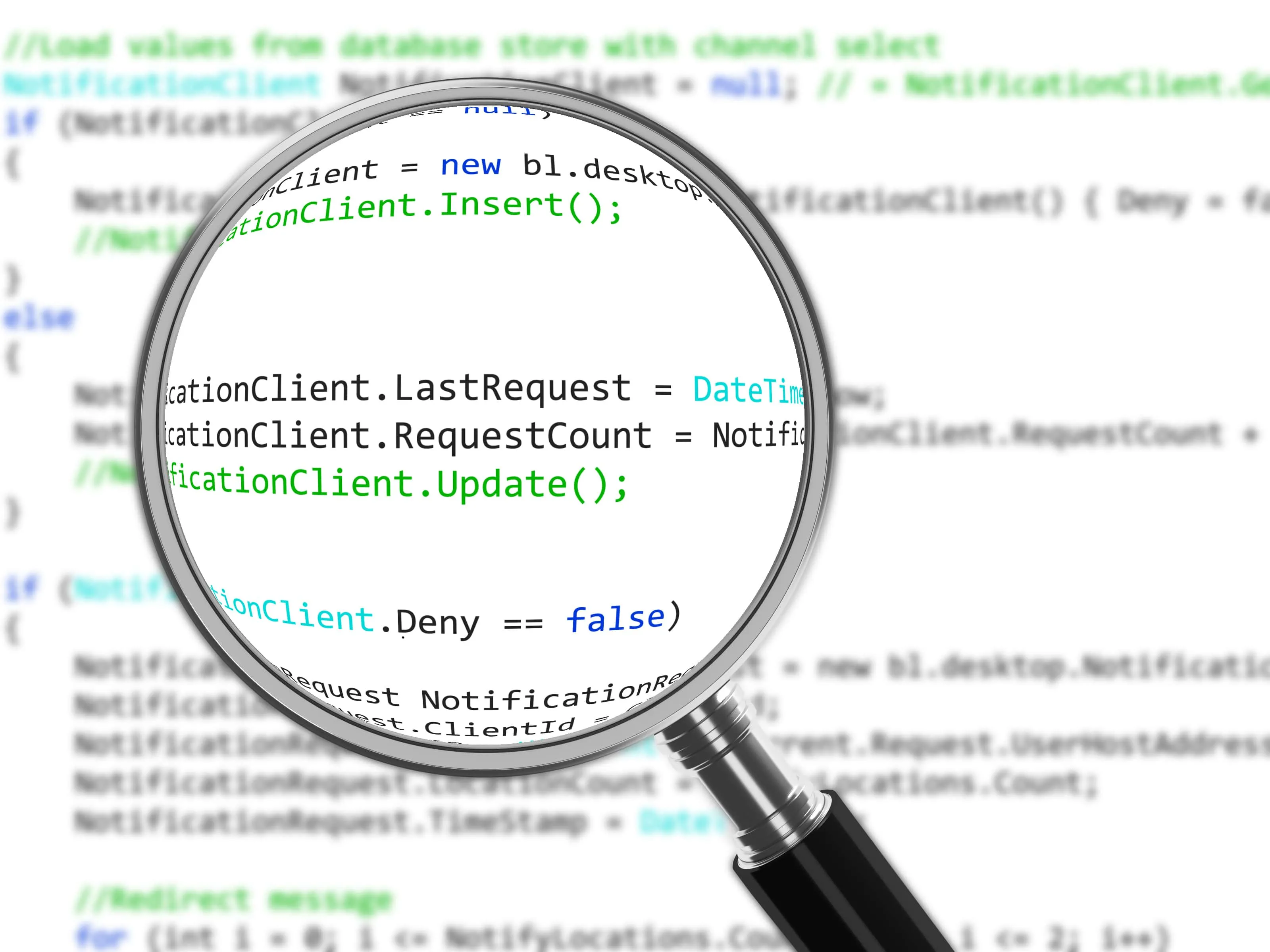
Through this training, participants will understand how Source Code Analysis (SCA) helps in identifying which statement on which line of code is vulnerable and the added advantage of identifying the tainted variable that introduces the vulnerability. We shall look into how SCA solutions provide application developers with an end to end overview of each instance of vulnerability, allowing them to quickly understand the nature of the problem.
What is Source Code Analysis (SCA)?
Source code analysis (SCA) not only identifies which statement on which line of code is vulnerable, but is also able to identify the tainted variable that introduces the vulnerability. In this way it illustrates the propagation from root cause, to end result. This provides application developers with an end to end overview of each instance of vulnerability, allowing them to quickly understand the nature of the problem.
Who should attend this training?
- Software Designers
- Application Developers
- Testers
- Security Team
- IT Managers
- Chief Information Officer (CIO)
- Senior Management
Why should you attend?
Source Code Analysis helps us to fix the issue at the source. Analysis of the web application source code for vulnerabilities and fixing them is the best solution to protecting your web application. Source Code Analysis solution helps us to:
- Scan the source code for all OWASP Top 10 vulnerabilities
- Report identifies exact function / line of code where the origin of the vulnerability exists helping fixing of code faster
- WAF plug-in helps protect web applications from the exploits while source code is being fixed
- Help to monitor website as normal user to check for malicious injection attacks and generate alerts to remove suspicious or malicious data
Prerequisites
Knowledge of OWASP Top 10 vulnerabilities would help to understand the risk impact more deeply.
Course Duration
2 Days
Table of Contents










Mohammed Harbi,student
I liked the instructor way for more illustration and the class was very interesting.
Yazeed, Senior Analyst
One of the best instructor, I have ever met.
Ali Al-Qahtani,
Thank you faculty. He has really gave us an excellent course by covering the material well.
Moataz Allami
Faculty is very knowledgeable instructor, enthusiastic and helpful.